YEREVAN (CoinChapter.com) — Zoth protocol, a restaking protocol focused on real-world asset (RWA) exposure, experienced a major exploit on March 21. The breach resulted in a loss of $8.4 million. The platform immediately took its website offline and moved to maintenance mode.
Blockchain security firm Cyvers flagged the suspicious activity. It traced the issue to the Zoth deployer wallet, which had been compromised. The hacker drained over $8.4 million in assets and quickly converted the funds to DAI stablecoin.
The Zoth team confirmed the hack in a public statement. It said the breach was a security incident and that they are working with partners to address the problem. The platform also said it would publish a full report after completing the internal investigation.
Zoth Hack Funds Moved to DAI, Then Ether
Minutes after the initial theft, the stolen funds were moved and converted. According to Cyvers, the attacker quickly swapped the assets into DAI and transferred them to another wallet. Later, blockchain firm PeckShield reported that the attacker swapped the DAI for Ether (ETH).
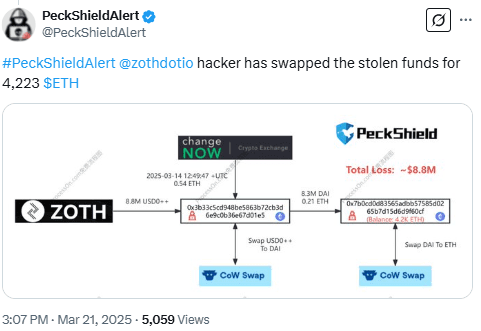
The attacker used an unlinked address and avoided centralized exchanges. The funds remain active on the blockchain, with no update yet on their destination.
Zoth protocol’s website has not returned from maintenance. Users have no access to services or any updated dashboard. There is no timeline for when the platform might return.
Admin Privilege Leak Caused Zoth Protocol Breach
According to Cyvers Alerts, the Zoth hack was caused by an admin privilege leak. Hakan Unal, Senior SOC Lead at the firm, said that about 30 minutes before the breach, a suspicious address upgraded one of Zoth’s contracts.
Subsequently, this upgrade replaced a secure contract with a malicious version, giving the attacker control over the system.
“This method bypassed security mechanisms and gave full control over user funds instantly,” Unal told.
This was not a common type of attack. Instead of breaking into user wallets, the attacker used access to admin-level privileges to drain assets directly from the restaking protocol.
Zoth Exploit Raises Concerns Over DeFi Admin Key Risks
Unal added that admin key compromises continue to threaten decentralized finance platforms. He pointed to the Zoth incident as an example of how attackers take control of privileged roles in smart contracts.
Unal explained that tools like multisig upgrades, timelocks, and real-time alerts can reduce risk. However, these features were not in place in this case.
As of yet, there is no confirmation yet on whether user funds will be recovered. Zoth protocol stated it is investigating the issue. The platform promised to release a full report once the internal review is complete.